Tenable Security Center
See everything. Predict what happens. Manage On-Prem.
Security Center
Understand your risk and know which vulnerabilities and assets to prioritise first with Tenable Security Center Plus. Get a risk-based view of your IT and OT security and compliance posture so you can quickly identify, investigate and prioritise your most critical assets and vulnerabilities.
Managed on-premises and powered by Nessus technology, the Tenable Security Center suite of products provides the industry's most comprehensive vulnerability coverage with real-time continuous assessment of your network. It’s your complete end-to-end vulnerability management solution.
Data is key in todays modern factory, SolutionsPT only partner with best in class vendors to deliver cyber security across the IT/OT boundary.
Active scanning, agents, passive monitoring, external attack surface management and CMDB integrations provide a complete and continuous view of all of your assets including ones that were previously unknown.
With coverage for more than 66,000+ vulnerabilities, Tenable has the industry’s most extensive CVE coverage and security configuration support to help you understand your security and compliance posture with confidence.
Tenable’s Predictive Prioritisation technology combines vulnerability data, threat intelligence and data science to give you an easy-to-understand risk score so you know which vulnerabilities to fix first.
The Tenable.sc Family
With options to meet security teams’ varying needs, the Tenable.sc suite of products gives you the visibility and context you need to understand your risk and fix vulnerabilities fast.
✅ Risk-based vulnerability management, on-prem
✅ Immediate visibility into your network with unlimited Nessus scanners
✅ Clear, actionable insight into data with highly customizable dashboards, reports and workflows
✅ Instantly identify and prioritize vulnerabilities using built-in risk scores and threat intelligence
✅ Speed up incident response with customizable configuration alerts, notification and ticketing
✅ Free API access for customer integrations, data acquisition and data enrichment
✅ Discover unknown assets on your External Attack Surface
✅ Gain a deeper understanding and context of your assets using Asset Criticality Rating (ACR)
✅ Real-time asset and vulnerability discovery and continuous monitoring for the highest level of visibility
✅ Streamlined compliance reporting with real-time metrics and proactive alerts on violations
✅ Real-time detection of botnets and command and control traffic
✅ Identification of previously unknown resources, changes in behavior and new application usage
✅ Single pane of glass to view and manage your network across all Tenable.sc consoles
✅ Easily manage scans for each Tenable.sc console from one central location
✅ Centralised network management to facilitate reporting and management of multiple consoles, scanners and assets
✅ Centralised reporting across multiple Tenable.sc consoles to easily measure your cyber risk

Tenable Security Center Plus is the leading on-prem option for Vulnerability Management. Manage your data your way with on-prem or hybrid deployment options while reducing risk for the organisation.
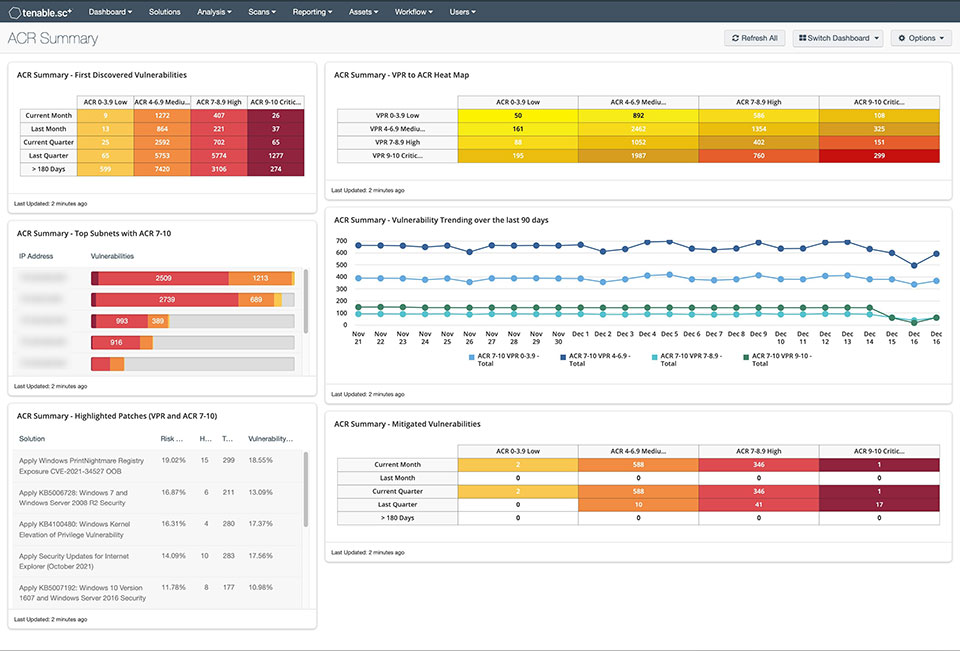
Tenable’s Asset Criticality Rating (ACR) in Tenable Security Center Plus provides an added dimension to understanding the criticality of your assets to make better decisions in reducing risk for your organisation.
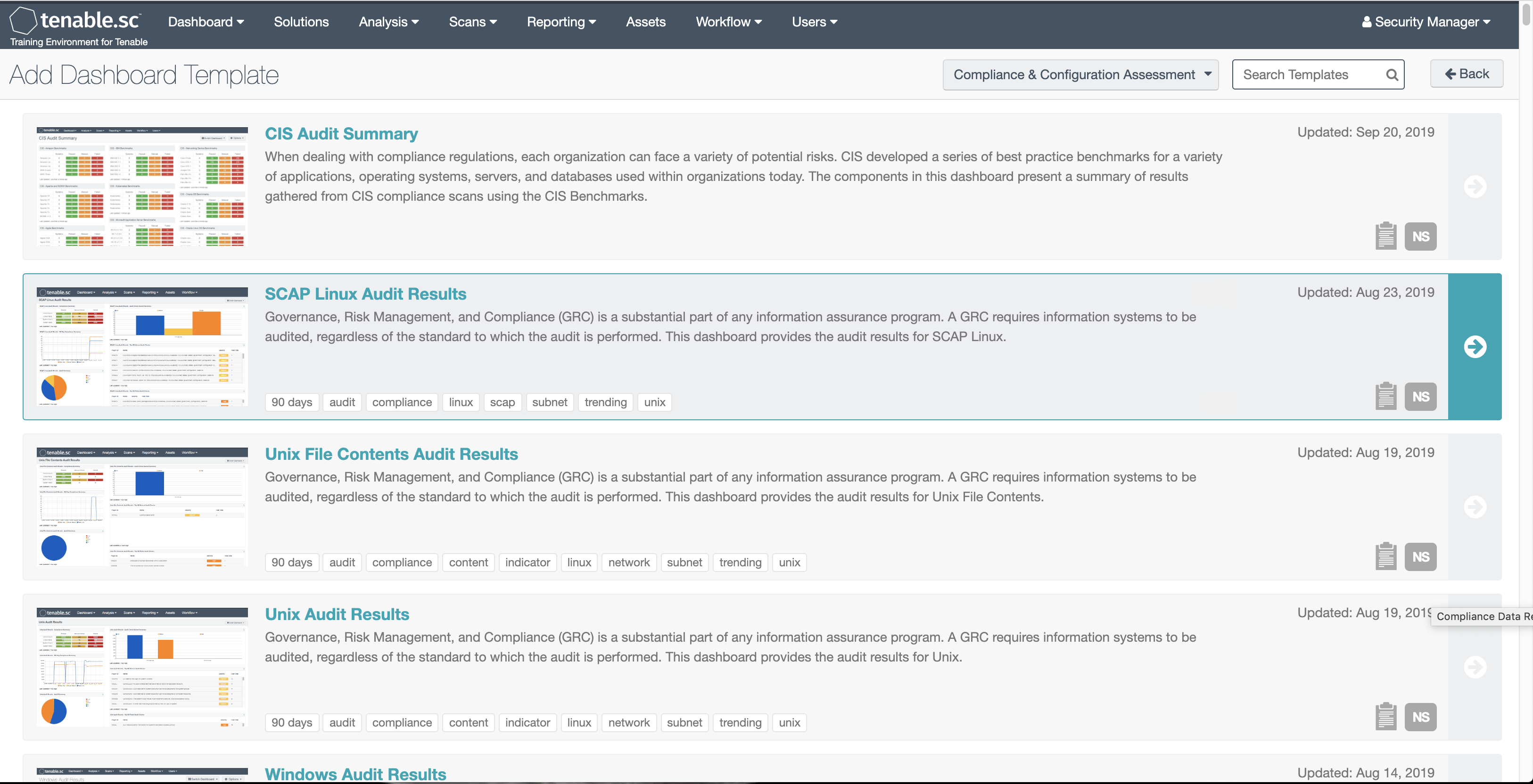
Leverage more than 350 pre-built, highly customisable dashboards and reports to get clear, actionable insight into the data you need to easily identify threats.
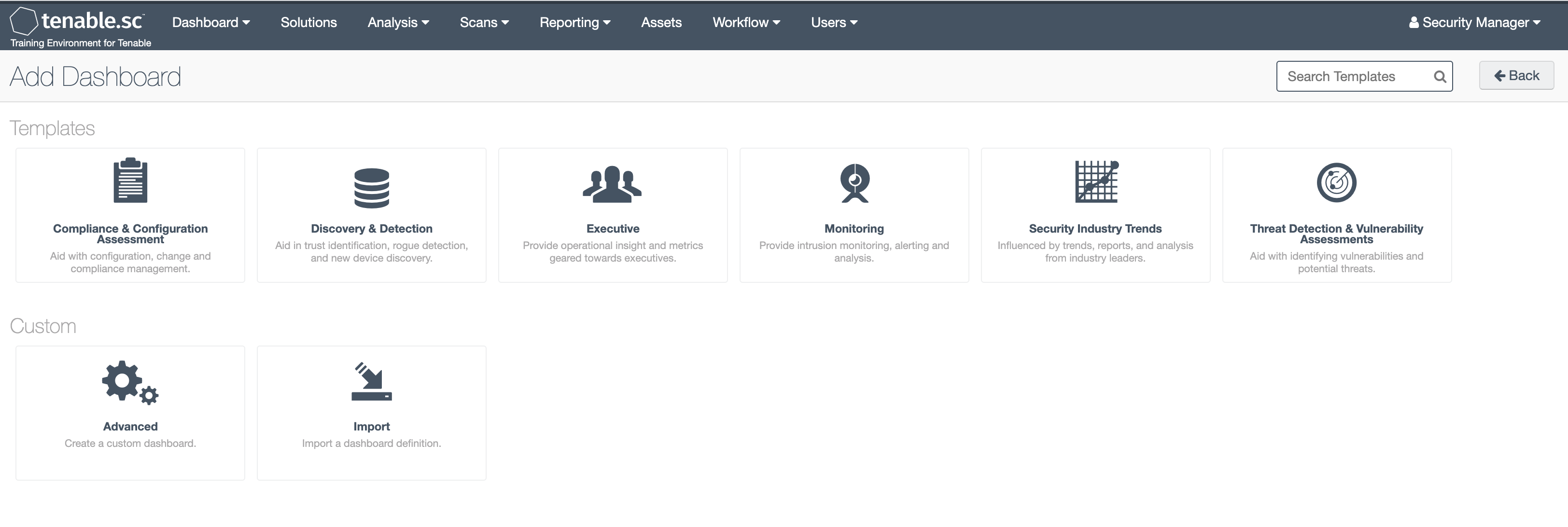
Create different reports for different audiences to ensure the most critical threats are seen and dealt with immediately. Generate reports on demand or schedule them, and automatically share with the appropriate recipients.
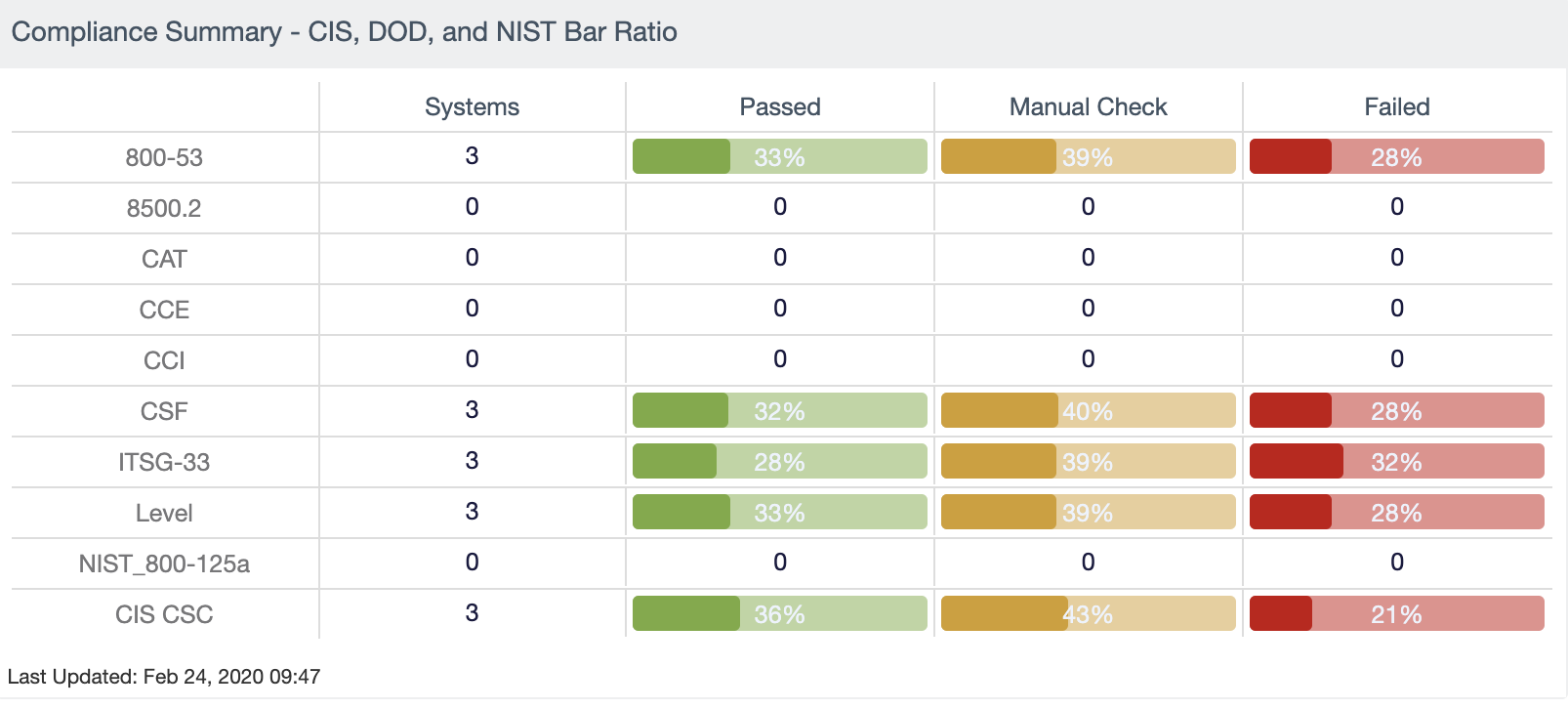
Stay compliant with immediate visibility into your compliance posture. Easily demonstrate adherence with predefined checks against industry standards and regulatory mandates.
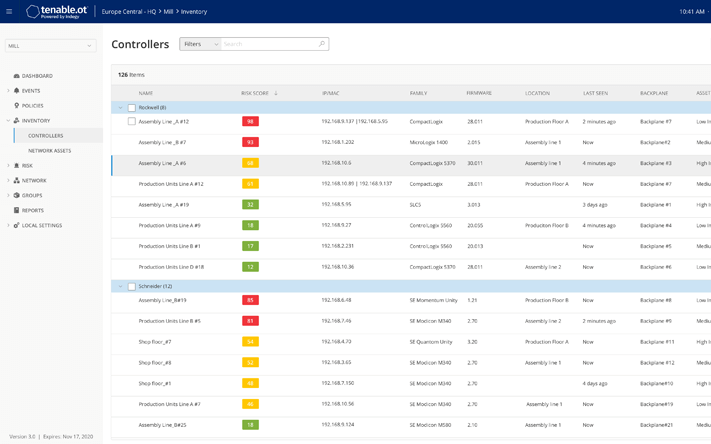
Gain complete visibility, security and control over the OT threats that put your organisation at risk with Tenable.ot integration.
Leverage Tenable's Ecosystem Of Trust
Leverage your existing security investments. Tenable OT Security fully integrates with Tenable Security Center and Tenable Vulnerability Management for full visibility, security and control across your converged operations. Tenable OT Security works in conjunction with Tenable.ad to identify Active Directory misconfigurations and threats which can result in ransomware attacks in OT environments. Tenable OT Security also has full integration with IT security technologies you already use such as IT service management, next-generation firewalls (NGFW) and security information and event management (SIEM) vendors.
With integration and collaboration across the Tenable product line as well as leading IT and OT security systems, you’ll gain full situational awareness needed to secure operations from today's IT and OT threats.

Asset Tracking
Tenable.ot’s automated asset discovery and visualisation capabilities provide a comprehensive, up-to-date inventory of all assets, including workstations, servers, human machine interfaces (HMIs), historians, programmable logic controllers (PLCs), remote terminal units (RTUs), intelligent electronic devices (IEDs) and network devices.
Tenable’s patented active querying capabilities discover dormant devices that do not communicate over your network. The inventory contains unparalleled asset information depth tracking firmware and OS versions, internal configurations, patch levels and users, as well as serial numbers and backplane configuration for both IT and OT assets.

Pinpoint Vulnerabilities
Proactively identify and remediate vulnerabilities before attackers exploit them. Drawing on comprehensive and detailed asset tracking capabilities, Tenable.ot uses a Vulnerability Priority Rating (VPR) that generates a score and triaged list of relevant threats.
This is based on the specific equipment in your environment, as well as parameters such as firmware versions, relevant CVEs, proprietary Tenable research, default passwords, open ports, installed hotfixes and more. Reports include detailed insights, along with mitigation suggestions.
Reduce the number of vulnerabilities requiring immediate remediation by 97%

Configuration Control
With Tenable OT Security you can track malware and user executed changes made over your network or directly on a device. Tenable.ot provides a full history of device configuration changes over time, including granularity of specific ladder logic segments, diagnostic buffers, tag tables and more.
This enables administrators to establish a backup snapshot with the "last known good state" for faster recovery and compliance with industry regulations.
Comprehensively Reduce Your OT Cyber Exposure With Tenable.ot
Often over 50% of your OT infrastructure contains IT assets. Attacks can easily propagate across IT/OT infrastructure.
Converged OT infrastructures require protection beyond OT. Leverage the Tenable product portfolio across the IT/OT boundary for enterprise-wide visibility and easy reporting.
Tenable.ot’s Vulnerability Priority Rating (VPR) identifies vulnerabilities and prioritises them. With real-time information, you’ll always know your risk profile and which vulnerabilities to handle first no matter where they are.
Tenable.ot with Nessus unifies your OT and IT security in an integrated solution that eliminates traditional blind spots and potential security risks. Map and disrupt the attack paths and configuration issues attackers most often leverage.
Reduction of Cyber Risk
When it comes to modern OT environments, cyberthreats can originate from anywhere and travel everywhere
IT and OT teams must find common ground to eliminate the substantial risk factors of both planned and accidental IT/OT convergence. OT security solutions that work in conjunction with IT security solutions can be the catalyst that not only provides the visibility, security and control needed to address new cyberthreats, but also brings these once separate teams together for the common security every manufacturing, critical infrastructure and industrial organisation needs to fulfill its core mission efficiently and secure.
Copyright © 2025 All Rights Reserved by SolutionsPT.








