Tenable OT Security for Critical Infrastructure
Industrial grade security for industrial operations and critical infrastructure
Manage IT/OT convergence with confidence
Disrupt threats with Tenable OT Security
Tenable OT Security is an industrial security solution for the modern industrial enterprise. Tenable OT Security gives your organisation the ability to identify your assets, communicate risk and prioritise action all while enabling IT and OT teams to work better together.
More than 50% of the assets in a modern factory are IT assets, with more IT departments becoming tasks with managing security of OT, there is a requirement to deploy tools that the enterprise is familiar with that protect production.
SolutionsPT specialises in Industrial IT, this is at the core of what we do, which is why we believe that the tools needed for successful digital transformation need to be suitable for both of these worlds.
Tenable OT Security offers comprehensive security tools and reports for your IT and OT security personnel and engineers. It provides unmatched visibility across IT/OT operations and delivers deep situational awareness across all global sites and their respective assets from Windows servers to PLC backplanes in a single interface.
Industrial Control Systems Require Industrial Grade Security
Detecting complex and evolving cyber threats requires advanced tools, knowledge and training. For example, OT environments contain more than OT. Up to half of the environment can also contain IT based devices. Stopping attacks and preventing damage require expertise and comprehensive security that can address both.
Read more about accidental convergence in this Guide to Secured IT/OT Operations.
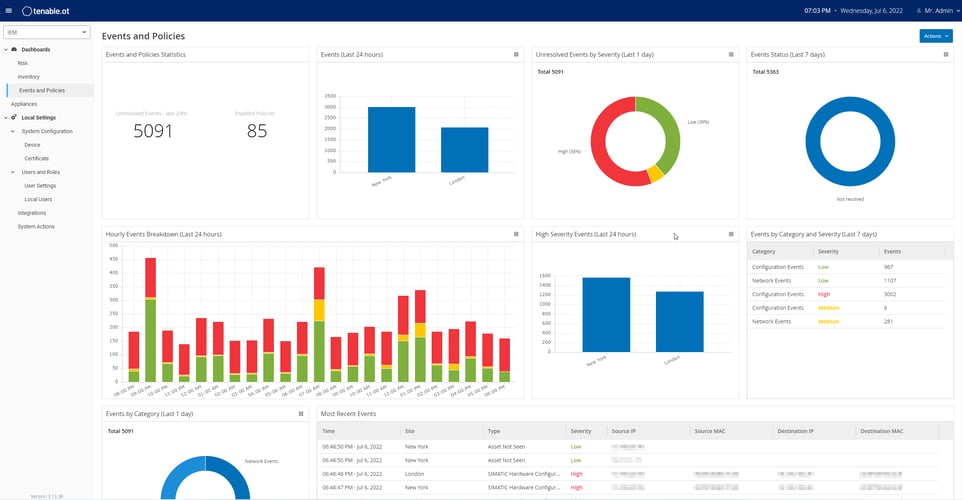
Enterprise Wide Visibility
Whether your organisation is a small one site location or has hundreds of sites across a complex and distributed environment, stopping an attack requires the ability to see it. In the past, siloed IT and OT security practices resulted in significant blind spots, thus limiting your ability to detect vulnerabilities and prevent attacks.
Tenable OT Security with Nessus eliminates blind spots and gives you a holistic view of your cyber exposure. Tenable.ot supports more than 90% of PLC products on the market today and has full integration with the Tenable product portfolio.
To leverage your existing IT security investments, Tenable OT Security also integrates with industry-leading enterprise IT security products.

Threat Detection And Mitigation
Proactively find weak spots in your OT environment by using Attack Vectors, which identify areas where an attack may be launched from or be taken advantage of.
Tenable.ot identifies anomalous network behavior, enforces network security policies and signatures and tracks local changes on devices so your organization can detect and mitigate risky events in your Industrial Control System (ICS) environments.
Context-aware alerts and detailed information give you the intelligence you need to meaningfully respond to threats based on full knowledge and details into what happened.

Attack vectors can proactively identify weak points in your OT environment before an attack ever occurs. Tenable OT Security's multi-detection engine identifies policy violations, detects anomalous behaviors and tracks signatures for potential high-risk events. Granular control allows you to set and fine-tune detection methods so they are optimized for your environment. With context-rich alerts, you can quickly respond and mitigate threats impacting your operations.

Tenable OT Security leverages domain expertise in industrial security for OT assets and Nessus for IT assets. Tenable’s VPR scoring generates vulnerability and risk levels using each asset in your ICS network. Reports include detailed insights, along with mitigation suggestions. This enables authorised personnel to quickly identify the highest risk for priority remediation before attackers can exploit vulnerabilities.
Leverage Tenable's Ecosystem Of Trust
Leverage your existing security investments. Tenable OT Security fully integrates with Tenable Security Center and Tenable Vulnerability Management for full visibility, security and control across your converged operations. Tenable OT Security works in conjunction with Tenable Identity Exposure to identify Active Directory misconfigurations and threats which can result in ransomware attacks in OT environments. Tenable OT Security also has full integration with IT security technologies you already use such as IT service management, next-generation firewalls (NGFW) and security information and event management (SIEM) vendors.
With integration and collaboration across the Tenable product line as well as leading IT and OT security systems, you’ll gain full situational awareness needed to secure operations from today's IT and OT threats.

Asset Tracking
Tenable OT Security's automated asset discovery and visualisation capabilities provide a comprehensive, up-to-date inventory of all assets, including workstations, servers, human machine interfaces (HMIs), historians, programmable logic controllers (PLCs), remote terminal units (RTUs), intelligent electronic devices (IEDs) and network devices.
Tenable’s patented active querying capabilities discover dormant devices that do not communicate over your network. The inventory contains unparalleled asset information depth tracking firmware and OS versions, internal configurations, patch levels and users, as well as serial numbers and backplane configuration for both IT and OT assets.

Pinpoint Vulnerabilities
Proactively identify and remediate vulnerabilities before attackers exploit them. Drawing on comprehensive and detailed asset tracking capabilities, Tenable.ot uses a Vulnerability Priority Rating (VPR) that generates a score and triaged list of relevant threats.
This is based on the specific equipment in your environment, as well as parameters such as firmware versions, relevant CVEs, proprietary Tenable research, default passwords, open ports, installed hotfixes and more. Reports include detailed insights, along with mitigation suggestions.
Reduce the number of vulnerabilities requiring immediate remediation by 97%

Configuration Control
With Tenable OT Security, you can track malware and user executed changes made over your network or directly on a device. Tenable.ot provides a full history of device configuration changes over time, including granularity of specific ladder logic segments, diagnostic buffers, tag tables and more.
This enables administrators to establish a backup snapshot with the "last known good state" for faster recovery and compliance with industry regulations.
Comprehensively Reduce Your OT Cyber Exposure With Tenable.ot
Often over 50% of your OT infrastructure contains IT assets. Attacks can easily propagate across IT/OT infrastructure.
Converged OT infrastructures require protection beyond OT. Leverage the Tenable product portfolio across the IT/OT boundary for enterprise-wide visibility and easy reporting.
Tenable.ot’s Vulnerability Priority Rating (VPR) identifies vulnerabilities and prioritises them. With real-time information, you’ll always know your risk profile and which vulnerabilities to handle first no matter where they are.
Tenable.ot with Nessus unifies your OT and IT security in an integrated solution that eliminates traditional blind spots and potential security risks. Map and disrupt the attack paths and configuration issues attackers most often leverage.
Reduction of Cyber Risk
When it comes to modern OT environments, cyberthreats can originate from anywhere and travel everywhere
IT and OT teams must find common ground to eliminate the substantial risk factors of both planned and accidental IT/OT convergence. OT security solutions that work in conjunction with IT security solutions can be the catalyst that not only provides the visibility, security and control needed to address new cyberthreats, but also brings these once separate teams together for the common security every manufacturing, critical infrastructure and industrial organisation needs to fulfill its core mission efficiently and secure.
Copyright © 2025 All Rights Reserved by SolutionsPT.