OPSWAT for Cybersecurity
Trust no file. Trust no device. Our Zero-Trust Philosophy.
OPSWAT is a global leader in critical infrastructure cybersecurity that helps protect the world’s mission-critical organizations from malware and zero-day attacks. To minimise the risk of compromise, OPSWAT Critical Infrastructure Protection (CIP) solutions enable both public and private organisations to implement processes that ensure the secure transfer of files and devices to and from critical networks.
More than 1,000 organisations worldwide spanning Financial Services, Defense, Manufacturing, Energy, Aerospace, and Transportation Systems trust OPSWAT to secure their files and devices; ensure compliance with industry and government driven policies and regulations; and to protect their reputations, finances, employees and relationships from cyber-driven disruption.
Trust no file. Trust no device.
We believe every file and every device poses a threat. OPSWAT solutions are engineered to support our zero-trust philosophy and powered by a comprehensive, modular suite of products to address a wide range of cybersecurity use cases.
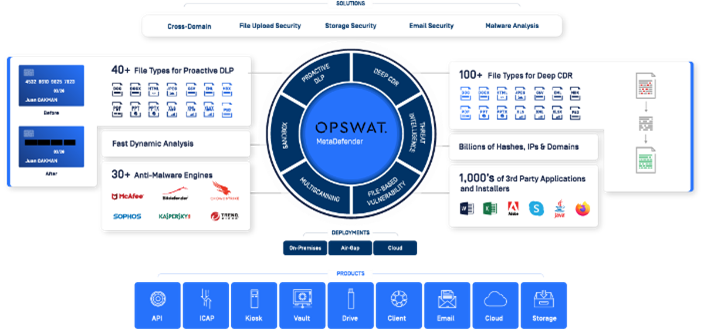
MetaDefender Platform
MetaDefender enables you to integrate advanced malware prevention and detection capabilities into your existing IT solutions and infrastructure for better handling common attack vectors:
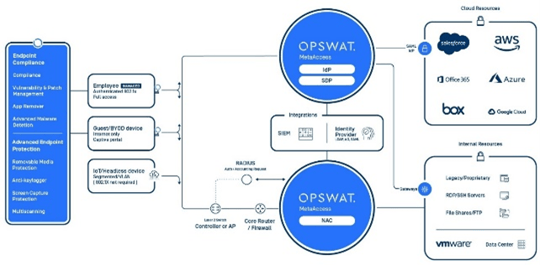
The complexities involved in maintaining visibility and control over what devices are accessing your network and are whether those devices are secure continue to grow, even more so with increased work from home scenarios.
Adding to the complexity is the myriad of point products generally needed to gain visibility and control.
MetaAccess is a comprehensive solution giving your organization secure network access and deep endpoint compliance. With this one platform approach, you can greatly simplify ongoing management, reducing time, effort and most importantly, risk.
MetaDefender Kiosk
MetaDefender Kiosk acts as a digital security guard—inspecting all media for malware, vulnerabilities, and sensitive data.

MetaDefender Kiosk accepts multiple form factors, including:
- CD/DVD, 3.5" diskettes
- Flash memory cards
- Mobile devices
- USBs—even when encrypted
MetaDefender Vault
MetaDefender Vault is a secure file storage and retrieval solution that protects critical data and keeps threats at bay. It limits access within an organisation and provides important tracking and auditing information.
-1-1-1.png?width=540&name=Blog%20(1)-1-1-1.png)
Storage You Can Trust
Transferring files into and out of any environment exposes systems to breach and infection. Portable media are often used to conduct these transfers, bypassing security protocols.
MetaDefender Vault is a secure file storage and retrieval solution that protects critical data and keeps threats at bay. It limits access within an organisation and provides important tracking and auditing information.
MetaDefender Drive
MetaDefender Drive is a portable USB stick that can boot, scan and inspect devices for malware, vulnerabilities and compliance issues. MetaDefender Drive facilitates a secure process for devices entering and leaving your air-gap networks to help protect your critical infrastructure.
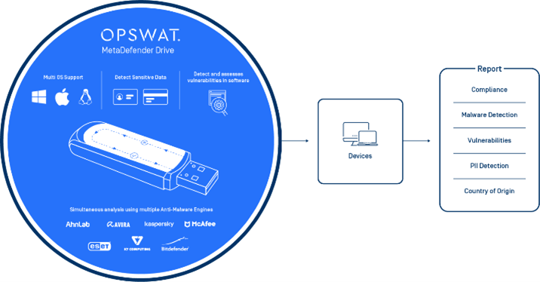
A Powerful Device Assessment for Malware, Vulnerability, and Sensitive Data.
The use of transient devices like laptops for data transfer or field operations while fulfills business needs, reveals a scenario where air-gap networks can be infiltrated. How do you as critical infrastructure organisation deal with this challenge?
MetaDefender Drive is built to help you! A portable USB stick that can boot, scan and inspect devices for malware, vulnerabilities and compliance issues, MetaDefender Drive facilitates a secure process of devices entering and leaving your air-gap networks, thus effectively helps protect your critical infrastructure.
MetaDefender USB Firewall
MetaDefender USB Firewall provides another option for safely and securely leveraging the productivity advantages, flexibility, and convenience of portable media in IT or OT SCADA environments.

Providing another option for securing and controlling portable media use in Critical Infrastructure
The MetaDefender USB Firewall from OPSWAT provides another option for safely and securely leveraging the productivity advantages, flexibility, and convenience of portable media in IT or OT SCADA environments.
Complementing OPSWAT’s MetaDefender Kiosk, MetaDefender Vault, and the OPSWAT Client for Windows, Linux, and Mac, the MetaDefender USB Firewall provides a plug-and-play, no install, no software footprint path to securing portable media; ensuring the boot sector and file contents of portable media are inspected, audited, sanitised, and approved prior to use.
MetaAccess NAC
MetaAccess NAC ensures that every network connection and endpoint device is visible, allowed, or blocked in real-time, reducing the threat associated with security incidents substantially.
Don’t risk your organisation’s data and reputation by exposing it –ensure the security of your network, your constituents’ personal information, and your intellectual property remains intact.
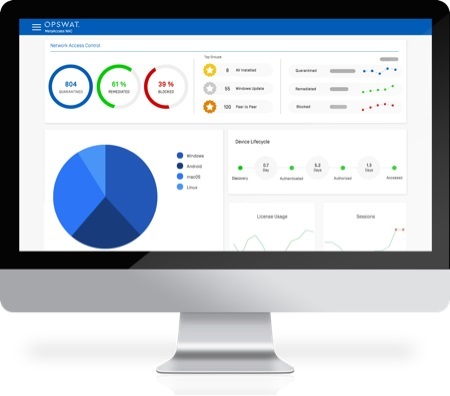
Why should you deploy Network Access Control (NAC)?
With the increasing number and type of devices accessing your network, it is important to provide visibility of all devices and where they are on the network. This prevents non-compliant or risky devices from accessing your network or applications. NAC solutions enable complete policy and device life cycle management.
What happens if I do not deploy a Network Access Control solution?
Without a NAC, it’s difficult to have confidence that you know everything on your network, can block unauthorised access, and all devices are secure. It’s also much more challenging to demonstrate compliance with internal policies and external regulations.
Data Sheets
Copyright © 2026 All Rights Reserved by SolutionsPT.